Trusted by Enterprises
Secure your IoT, Unmanaged, OT and BioMed devices for 50%-75% less cost than Competitors.
100% Device Visibility
Shadow IT, defined as unknown endpoints on a network, is a significant problem most networks face. However, a device doesn’t need to have been placed with nefarious intent to pose a threat to other devices and computers on the same network. To combat this problem, IT Asset Inventories are crucial. IoTSecure’s solution will help you get complete, accurate, and up-to-date inventories to find the unexpected, unknown, and unmanaged devices on your network before malicious actors do.
Identify All Managed, Unmanaged & IoT Devices
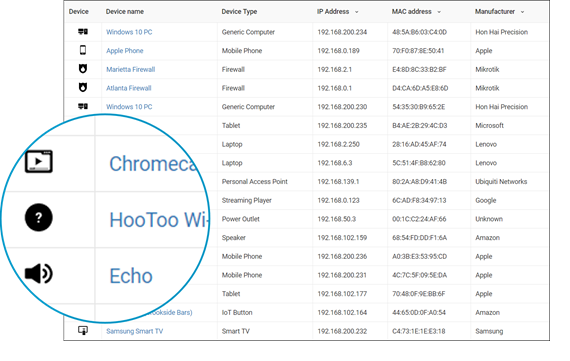
- IoTSecure tells you when a device connects and exactly what it is. No more manual device inventory.
- Because you’ll see every device, finding shadow IT is easy. And, you don’t need to worry about accurately identifying devices because IoTSecure even profiles devices that encrypt traffic or that have 3rd party NICs.
- Now, you can alleviate problems with finding vulnerable devices that have moved since they was last scanned. Because IoTSecure automatically tracks devices, you can find them wherever and whenever they move.
Safe Vulnerability Detection
Any moderately mature IT security program has some kind of vulnerability management they do. Usually by running one of the well-known vulnerability scanners, like Nessus or Qualys, against all the systems on the network. The problem is that while these scanners are great at working with the systems they expect, servers, workstations, etc., they do not play well with other connected devices like IoT. IoTSecure saw this problem and developed our solution to help find these non-traditional devices specifically.
Safe, Active Inspection Designed for IoT
Traditional vulnerability scanners often need agents for in-depth scanning. Also, they can overwhelm and crash devices or force IT to exclude them from scans. Either can lead to incompletely tested or untested devices on the network.
IoTSecure’s IoT PortSafeTM was designed just for sensitive IoT devices that don’t run agents. It first understands what the device is and how to safely test it, before any testing occurs. With this knowledge, it then can gently test the device to detect IoT vulnerabilities precisely, intelligently and non-intrusively. And, it does so as devices connect so there you know right away when a vulnerable device connects to the network vs. waiting until the next scheduled vulnerability scan.
sample checks:
- default credentials
- hard-coded credentials
- open/unwanted services
- manufacturer back doors
- eternalblue / ransomware
- remote code execution
- bluekeep, vxworks, etc.
- rdp & ssl vulnerabilites
- unsecured document access
Automated Behavior Monitoring
For as long as network security standards have existed, the first and most important aspect is the control and management of those assets. Because of the core nature of this tenant, the tools that do this for traditional IT endpoints, like servers and workstations, are well-made and do the job well. But, when you look at the litany of other endpoints on a modern network, like IoT, OT, ICS/SCADA, BioMed, and the endless list of “smart” devices, these traditional tools do not do such a good job. Find out what is on your network, EVERYTHING, today with IoTSecure.
Device-level monitoring is no longer a tedious and manual process involving manual device behavior analysis and security rules

IoTSecure automates the process. The results are automated and high-fidelity alerts to protect the environment when a devices misbehaves.
- suspicious communications
- malicious communications
- abnormal communications
- CVE & CERT advisories mapped to devices
- restricted devices
- network hopping
- restricted OS
Integrate & Manage Existing Tools
Most security programs are good at maintaining, monitoring, and securing their traditional endpoints (servers, Laptops, networking equipment, etc.). These more conventional devices can run software agents and be managed centrally with tools like Active Directory. However, IoT, OT, BioMed, and other connected devices are not so equipped. These less powerful endpoints can’t run agents, and their access cannot be managed centrally until now. IoTSecure has developed our solution from the ground up to help you manage and secure your unmanaged devices.
Two ways to secure IoT devices which one is right for you?
Leverage existing tools to take control of IoT
- IoTSecure can integrate device and threat detail with other solutions that your team is already using. So, you’ll have the context needed to make fast & informed decisions, while in the case of NAC, have a means to block, segment and control devices.
Remediate Unpatch-able IoT devices
- Once a security threat is identified, IoTSecure can automatically create and share a compensating control to remediate the vulnerability while leaving the device operational. Additionally, IoTSecure uniquely does this for passive, behavior-based threats and threats discovered through our active inspection.
million +
0Secured users
million +
0Profiled devices
million +
0Vulnerabilities detected
Watch why IoTSecure is the right solution to help you get control of your connected and IoT devices.

Latest Blogs
From thought leaders in the cybersecurity industry.
xIoT: The Next Phase of Healthcare Security
If you are a healthcare executive such as a CEO, CFO, or senior leader responsible for the strategic and operational health of your organization, this..
Read MoreHackable Cardiac Implants: We Could Have Helped
Your heart isn't working like it used to, so the doctor recommends a cardiac implant to regulate how your cardiovascular system works. But, unfortunat..
Read MoreThe Mirai Botnet: We Could Have Helped
The botnet was used for its first big wave of attacks on September 19th, 2016, against the French internet hosting company OVH. It was later revealed ..
Read MoreMake IRS 1075 Compliance Easier!
If you are a tax preparer, vendor, or tax auditor that handles any information from the United States Internal Revenue Service, especially federal tax..
Read More